Internet’s DNS Infrastructure Attacked with 5 Million Queries a Second
Early last week, one of the most critical organs to operate the Internet ecosystem came under an unusual attack. A flood of nearly five million queries per second hit various domain name system (DNS) root servers that act as the final and authoritative reference for determining which IP address is returned when a user types a domain name into their browser.
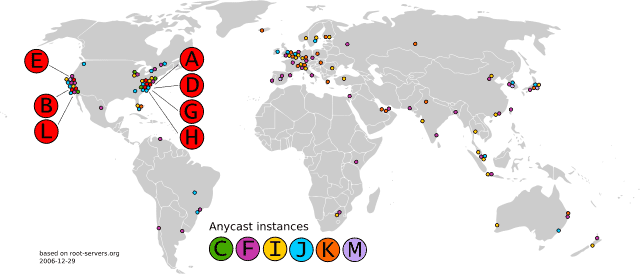
Attackers hit the services on two separate occasions, the first of which took place on Monday, November 30, and lasted for nearly two hours and forty minutes. A majority, but not all of the 13 root servers that form the Internet’s DNS root zone were hit struck by the massive DDoS attack. The second DDoS attack struck the batch servers again on December 1 and lasted for nearly an hour.
While the attack sent a substantial load of traffic to be detected by an external system monitoring the Internet’s backbone, they ultimately had little to no effect on the massive root servers pushing billions of queries per day. The attack did, however, knock out 3 of the 13 DNS servers for a couple of hours.
Despite having little to no impact on end users the attack was by no means casual. An attack with the sheer computing power of five million queries per second that can actively attack root servers for hours on end represents an alarming amount of power.
“This event was notable for the fact that source addresses were widely and evenly distributed, while the query name was not,” an advisory published by server operators on Friday noted. “This incident, therefore, is different from typical DNS amplification attacks whereby DNS name servers (including the DNS root name servers) have been used as reflection points to overwhelm some third party.”
According to the report published by the root server operators, each attack flooded up to 5 million queries per second to each DNS root name server and was able to disrupt root servers B, C, G and H.
“The DNS root name server system functioned as designed, demonstrating overall robustness in the face of large-scale traffic floods observed at numerous DNS root name servers,” DNS server operators said in their report, referring to the backup system employed in the event of an attack.
In the end, the DDoS attack caused minor damage and merely delayed some requests for Internet users who made DNS queries through their browser, FTP, SSH, among other clients.
The motive for such a large scale attack is unclear, as disabling a primary DNS operator would not have severe impact on the Internet ecosystem as there are countless other DNS servers effectively handling DNS queries. As well, DNS servers handle attacks similarly to many Internet infrastructures today, allowing other servers to step in and provide help in the event another server is malfunctioning or timing out.
A massive botnet of infected machines alongside other Internet-connected devices in the most plausible explanation for such a high-power attack from such a diverse range of addresses. An attack this scale has not been seen, especially attacking such an unusual part of the Internet.
The DNS root server operators called for Internet Service and network providers to implement BCP 38, an Internet Engineering Task Force standard that defeats IP address spoofing. Many networks enforce these policies, however the ones that don’t enable such attacks to be possible.
[Photo via BTC Keychain/Wikimedia (CC BY-SA 3.0)]