Facebook Creates Hidden Service .Onion Domain, Accessible via Tor Network
In a bizarre turn of events, Facebook, the largest Social Network in the world with over one billion registered users, has created a deep web style Facebook accessible exclusively through the Tor Network.
The Tor Project is an anonymity network that routes users internet-traffic around the world, leveraging thousands of nodes encrypting users traffic with each hop. The Tor Project anonymizes users identity while allowing them to safely browse the web. The Tor Network allows users to connect to anonymized web-servers located under the ‘.onion’ top level domain (TLD) . Such servers hosting onion domains are referred to as Tor Hidden Services.
For reasons in the past, Tor Network users who wished to sign into Facebook may have run into problems, due to IP’s being ban among a number of security issues. Many reasons Facebook users had a tough time logging in through Tor was due to security measures, all restrictions were well-intentioned security measures on Facebook’s end.
“Tor challenges some assumptions of Facebook’s security mechanisms – for example its design means that from the perspective of our systems a person who appears to be connecting from Australia at one moment may the next appear to be in Sweden or Canada. In other contexts such behaviour might suggest that a hacked account is being accessed through a ‘botnet’, but for Tor this is normal,” Alec Muffett, Software Engineer for Security Infrastructure at Facebook London, wrote in the company’s official statement.
Facebook made it clear their onion domain is currently in an experimental phase, meaning there are likely bugs they need to work out in the coming weeks.
Facebook’s move towards hidden services is not the only innovation the company is moving towards. Facebook’s .onion domain will connect its users to Facebook’s core infrastructure. This means users will be connecting to Facebook’s datacenter directly, rather than the traditional method of routing through an exit relay.
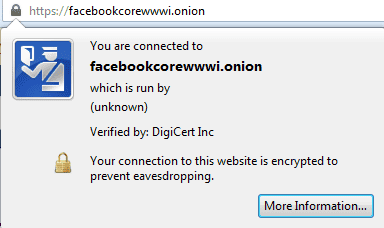
To stop fraudulent deepweb Facebook websites from appearing and hijacking credentials, Facebook has stocked its hidden service website with a custom SSL certificate, assuring users connect to the real Facebook while stopping SSL certificate warnings.
Privacy and security researcher Runa Sandvik noted on Twitter that the launch of Facebook’s Tor hidden service marks the first time a certificate authority has issued a legitimate SSL certificate for a .onion domain address. DigiCert issued Facebook’s hidden service onion domain their SSL certificate.
Facebook’s users have not taken to the company’s latest news and innovations. Many users throughout comments have outed Facebook for the endless privacy violations and have stated the company wants to further impose surveillance on the Tor anonymity network.
Users were also worried that Facebook was able to brute force a key for facebookcorewwwi.onion, making it possible for others to come along and brute-force the same hostname. Roger Dingledine of the Tor Project wrote a post on the Tor Project list regarding concern, stating Facebook generated keys over and over until the company got some keys whose first 40 bits of the hash match the string they wanted.
Furthermore, Dindledine stated “they would not be able to produce exactly this name again if they wanted to. They could produce other hashes that started with “facebook”, but that’s not brute forcing all of the hidden service name (all 80 bits).”
To access Facebook’s new deepweb .onion domain, https://facebookcorewwwi.onion/, users must first connect to the Tor Network.






Facebook’s business is to get as much data as they can about everyone. They’re also known to run a ridiculous number of experiments on their live users any given moment. Their stance on privacy is also well known: undermine it wherever possible. Given these, the most likely explanation is that they’re going to apply their datamining techniques to Tor users. They’ll study them in isolation, try to correlate them with facebook users in many ways, possibly target ads/products/services directly toward this niche, and possibly work with NSA in attacking them. That’s my guess.