Web Tracking Gets Extremely Aggressive with New Hardware Level Fingerprinting
Online web tracking has gotten even more aggressive overnight, as a group of researchers have developed a browser fingerprinting method so intrusive, it tracks you at the hardware level. The newest technique, which currently cannot be blocked, allows for websites to track visitors even if they are using two entirely different browsers.
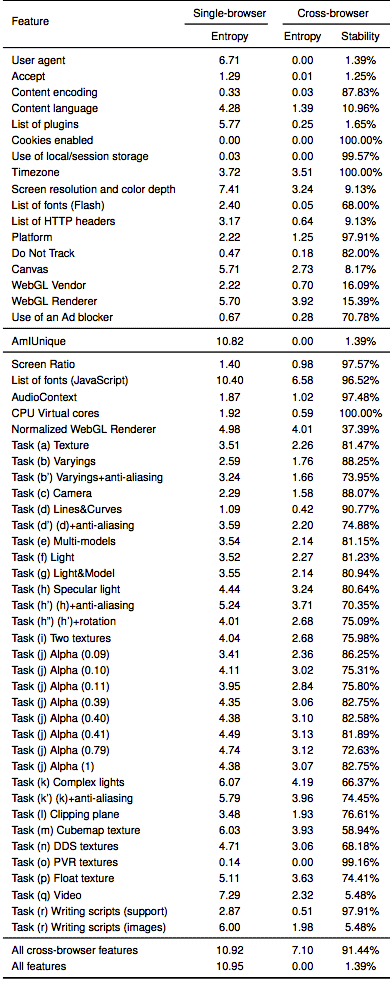
Browser fingerprinting is one of the most effective techniques at identifying individuals across the web to date. This is due to the way browsers interact with websites to make them function properly. To visualize how fingerprinting works, the Electronic Fronter Foundation has a free privacy tool known as Panopticlick. The service measures how effective your browser is against online web tracking, and more specifically fingerprinting. Results vary based on every specific setting on your computer, including everything from fonts, to specific plugins, to time zones and the site can actually give you your fully identifiable fingerprint.
Up until this point, while this tracking is extremely aggressive, it’s always been constrained to one browser. This means that if you used a service in Firefox, and then did the same thing in Chrome, you wouldn’t be identifiable specifically due to your browser. In the latest technique outlined by researchers, in a paper titled (Cross-)Browser Fingerprinting via OS and Hardware Level Features, researchers are able to identify users across multiple browsers. The latest technique is actually more accurate than previous fingerprinting methods available right now.
Fingerprinting isn’t inherently evil, and can, at select times, offer potential benefits to you. An example of this would be with banks, tracking fingerprints to know if the person logging into the account is actually you and not an unknown device. Based on automation techniques, banks are actually able to identify suspicious activity in real-time and contact account holders to confirm the device is in fact them. However, not every website you visit a bank, which poses huge privacy concerns.
“From the negative perspective, people can use our cross-browser tracking to violate users’ privacy by providing customized ads,” Yinzhi Cao, the lead researcher who is an assistant professor in the Computer Science and Engineering Department at Lehigh University, told Ars. “Our work makes the scenario even worse, because after the user switches browsers, the ads company can still recognize the user. In order to defeat the privacy violation, we believe that we need to know our enemy well.”
The new technique relies on code that instructs each browser to perform a variety of system tasks. These tasks can actually impact system and hardware performance, these include tasking the graphics card, multiple GPU cores, audio cards, and system fonts, which can vary greatly for each computer. The cross-browser fingerprinting carries out 36 new features to track browsers, 20 of which use the WebGL standard for rendering 3D graphics in browsers.
Researchers explain how these tasks work in their paper, detailing:
We propose a (cross-)browser fingerprinting based on many novel OS and hardware level features, e.g., these from graphics card, CPU, audio stack, and installed writing scripts. Specifically, because many of such OS and hardware level functions are exposed to JavaScript via browser APIs, we can extract features when asking the browser to perform certain tasks through these APIs. The extracted features can be used for both single- and cross-browser fingerprinting.
99% Success Rate on Average
The cross-browser tracking technique relies on compacted JavaSctipt code that can quickly be ran in the background while visitors focus on their web page, such as reading an article or viewing a video. The researchers launched a website to demonstrate the techniques live, and released the corresponding, now, open-source code. In a test that collected 3,615 fingerprints from 1,903 individual users over a three month period, the techniques were able to identify users with a 99.2% success rate. By contrast, previous techniques that rely on single-browser fingerprint known as AmIUinque, had a success rate of 90.8% on the same test group.
One upside is cross-browser tracking doesn’t affect the default installation of the Tor browser, leaving Tor as a somewhat viable privacy solution. A portion of users that use Tor regularly will often times slightly modify their Tor browser to make it more accessible to the web, however, the latest techniques could de-anonymize a whole lot of Tor users extremely quick. Cao said he is not aware of any sites that currently deploy cross-browser fingerprinting.
Cross-browser fingerprinting is only the latest tool developers can add to their evil toolbox of extremely identifying techniques. Tracking has gotten far more aggressive over the past year techniques including TV commercials trying to inject inaudible sounds to track devices across specific locations, or the rate at which people type in their browser. Yes, the way you type is identifying.
The best defense against these latest cross-browser fingerprint techniques is to use the Tor browser, although researchers did note that running browsers inside a virtual machine could also prevent the tracking.
“This approach is lightweight, but we need to find all possible fingerprintable places, such as canvas and audio context,” researchers said, theorizing over the virtual machine defense. “If one place is missing, the browser can still be somehow fingerprinted. We leave it as our future work to explore the correct virtualization layer.”