Lone Hacker Takes Dark Web Host Offline, Killing 10K .onion Domains & Leaking Databases
Friday morning, a lone hacker claiming to be part of the Anonymous hacking group, took down one of the dark webs most prominent hosting providers, Freedom Hosting II, a provider that is estimated to host nearly 1/5th of the active dark web.
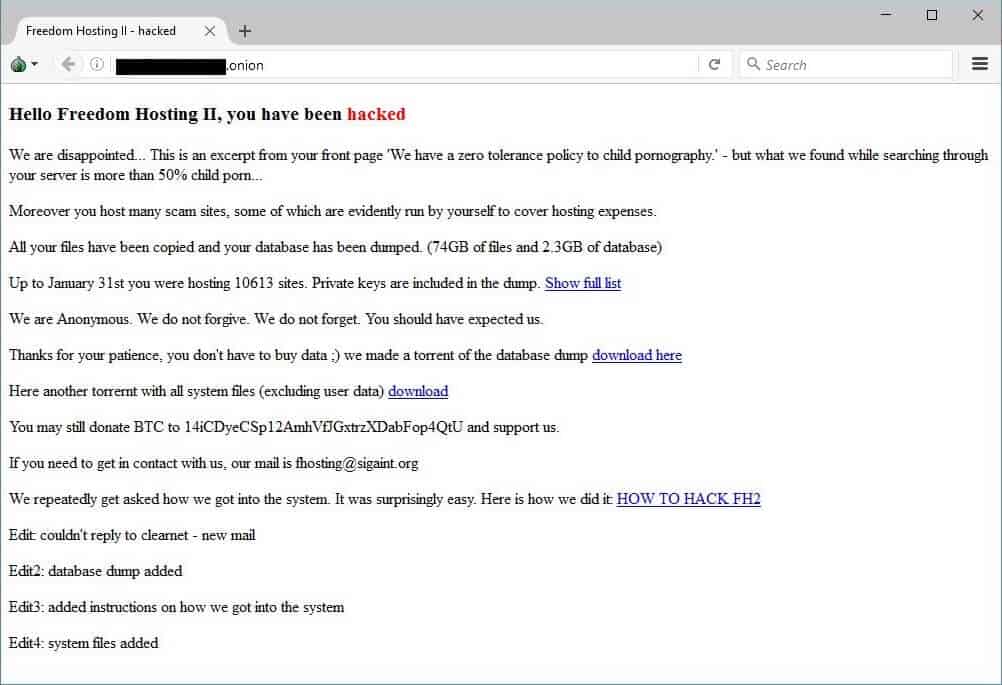
The unknown hacker, who has claimed to be a sole individual, replaced Freedom Hosting II’s homepage with a friendly, “Hello, Freedom Hosting II, you have been hacked.” The hacker claimed to have stolen all the hosting service’s databases, initially holding it ransom for 0.1 bitcoin (roughly $100).
Following the deface, the hacker suddenly altered their message, making all the databases public. The hacker linked to a torrent file which has since been shared tens of thousands of times.
The catastrophic darknet leak is said to include email addresses of some 381,000 users, according to Troy Hunt, a security researcher who runs the popular Have I Been Pwned service. A website that takes public data breaches and securely stores the information, allowing anyone to easily search if their online account has been compromised and leaked online.
Freedom Hosting II was one of the single largest darknet hosts online to date, allegedly hosting somewhere near 15-20% of all hidden services online, privacy researcher Sarah Jamie Lewis estimated. 10,899 .onion addresses were taken offline when Freedom Hosting II went black.
In an interview with Motherboard, the Anonymous hacker who claimed responsibility for taking Freedom Hosting II offline said it was his first ever hack, and he never intended to take the entire provider offline.
He said after scouring through the databases he stumbled upon a large collection of child pornography sites, most using far more storage than average Freedom Hosting II customers were allocated. Following his investigation, he felt it was his duty to take the service offline.
According to the Anonymous hacker, more than 50% of the sites on Freedom Hosting II were related to child pornography. The illicit sites were allowed several gigabytes of storage, which is odd as Freedom Hosting II restricted users to no more than 256MB per site. Suggesting the owner was aware and allowed the content.
In addition to user emails being leaked, the dump contained more critical data including full website databases, most of which are popular & open-source content management systems including Wordpress and PHPBB.
Nearly 21 percent of the email addresses leaked online were found in previous data breaches, suggesting many are legitimate people’s everyday email address. In a tweet, Troy Hunt pointed out that there were thousands of .gov email addresses, explicitly asking “how many are real and what purposes they were being used for is another issue.”
According to Hunt, much of the data within the torrent is highly explicit, as more than half of the sites were alleged to be hosting child pornography.
Freedom Hosting II was the reincarnation of the original Freedom Hosting, a massively popular darknet hosting provider who was described as hosting some of the most “extremely violent and graphic” child pornography sites on the dark web.
One thing that needs to be clear is that Tor and hidden services are not only used for crime and horrific illicit activities described above, but are often used by whistleblowers, political dissidents, and those trying to escape aggressive censorship.
The Freedom Hosting II dump is most certainly in the hands of law enforcement by now, as this data is extremely public and contained huge portions of real email addresses. It’s inevitable this hack will have an extreme impact and some users may be getting more than just a knock on their door very soon.
As for how, the hacker laid out their simple 21 steps to hacking Freedom Hosting II:
“here is how we did it:
1. create a new site or login to an old one
2. login and set sftp password
3. login via sftp and create a symlink to /
4. disable DirectoryIndex in .htaccess
5. enable mod_autoindex in .htaccess
6. disable php engine in .htaccess
7. add text/plain type for .php files in .htaccess
8. have fun browsing files
9. find /home/fhosting
10. look at the content of the index.php file in /home/fhosting/www/
11. find configuration in /home/fhosting/www/_lbs/config.php
12. copy paste database connection details to phpmyadmin login
13. find active users with shell access in /etc/passwd
14. look through the scripts and figure out how password resets work
15. manually trigger a sftp password reset for the user ‘user’
16. connect via ssh
17. run ‘sudo -i’
18. edit ssh config in /etc/ssh/sshd_config to allow root login
19. run ‘passwd’ to set root password
20. reconnect via ssh as root
21. enjoy”






Supremely excellent investigative and reporting work! Hooray for those who take down child porn sicko’s!
You did good, once more, Anonymous!