Stealthy Malicious Ads Strike Massive Sites Including Ebay, Drudge Report, Answers.com in Undetected Three Week Attack
Around mid August, a group of actors behind many recent malvertising campaigns began to roll out several new features, allowing them to fly under the radar and infect users visiting some of the worlds most popular sites, exposing tens of millions to malware.
Due to the increase and scrutiny on malvertising and ad networks, criminals have had to revise their plans, a critical part in how the malicious actors continue to infect and abuse millions.
The malicious ad campaign ran largely undetected for nearly three weeks time, according to data researchers at Malwarebytes blog were able to uncover.
The attackers leveraged several top ad networks, deploying extremely stealthy techniques posing as legit advertisers to direct browsers to the Angler Exploit Kit, the most advanced tool used in drive-by download attacks.
Companies the attackers were posing to be had domains registered years before with some even being listed in the Better Business Bureau registry. Their techniques fooled several ad networks, exposing attackers to tens of millions of machines.
Ads shown on top-domains were loaded directly from the rogue advertisers’ websites, yet the ads were not booby trapped in any way, making it extremely difficult to spot suspicious activity.
According to security researches at Malwarebytes, the list of affected websites includes:
| Site Name | Monthly Traffic (according to Similarweb) |
|---|---|
| ebay.co.uk | 139M |
| drudgereport.com | 61.30M |
| answers.com | 53.8M |
| nuvid.com | 51.50M |
| upornia.com | 35.80M |
| wowhead.com | 27.8M |
| ehowespanol.com | 20.30M |
| legacy.com | 18.4M |
| eroprofile.com | 15.60M |
| newsnow.co.uk | 15.50M |
| talktalk.co.uk | 11.10M |
| pornyeah.com | 10.60M |
| manta.com | 9.8M |
| iceporn.com | 7.50M |
| streamsexclips.com | 5M |
| xbabe.com | 4.40M |
Attackers also abused a number of the biggest ad networks in the industry, alongside smaller players including:
- DoubleClick (ad-emea.doubleclick.net)
- AppNexus (fra1.ib.adnxs.com)
- engage:BDR (delivery.first-impression)
- ExoClick (syndication.exoclick.com)
- adk2x.com
- rtbfy.com
- ecpmrocks.com
- teracreative.com
To get a better understanding on how the malicious ad funnel worked, researchers put together a small graphic that can be seen below. Techniques deployed in their attacks were similar to their previous, however they put great care into masquerading their domains to avoid detection, such as encrypting their site traffic with HTTPS certificated among various other advanced tricks.
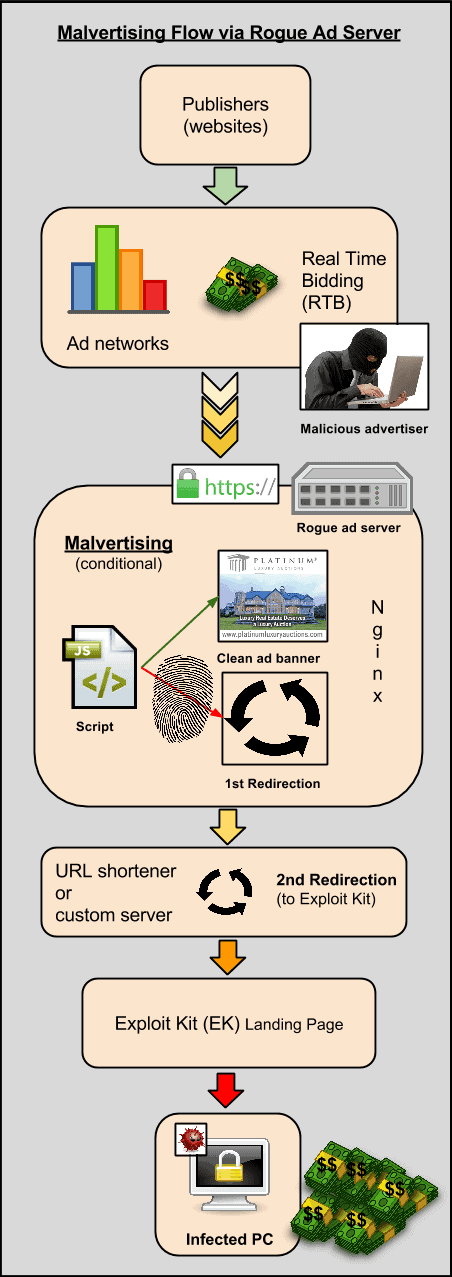
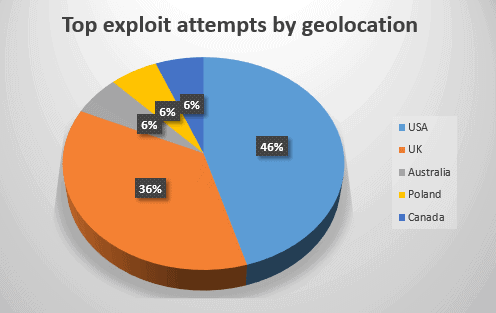
Victims visiting the rogue domains were instantly infected by the Angler Exploit Kit. Among the kits were typical ad fraud and ransomware, attempting to target and exploit users throughout the US and UK.
While these actors continue to break headlines, these attacks are only the beginning into the dangerous world of malware. Some campaigns on the market are so advanced that we will never see or hear about them as no one will be able to detect them, exactly what these attackers are hoping for.
Just a scary reminder on how dangerous advertisements on even the worlds most trusted domains can be, even successfully infecting tens of millions of visitors.






