Ouch! Nasty POODLE Variant Bypasses TLS Crypto Affecting Over 10 Percent of the Web
A new variant of the POODLE attack has come to light and is affecting the world’s leading websites including, Bank of America, the United States Department of Veteran’s Affairs, VMWare among others allowing attackers to bypass the transport layer security (TLS) encryption which is designed to thwart eavesdroppers and attackers.
The attack is a so-called variant on the previous POODLE exploit, POODLE short for “Padding Oracle On Downgraded Legacy Encryption,” was an SSL 3.0 exploit that allowed attackers to bypass the SSL 3.0 protocol and recover plaintext communications sent over the network. Attackers could easily decrypt HTTPS traffic sent over the fifteen year old protocol.
Many companies along with browsers responded quickly, limited or disabling SSLv3 entirely, a move that helped thwart the attack quickly, making it almost disappear two months ago.
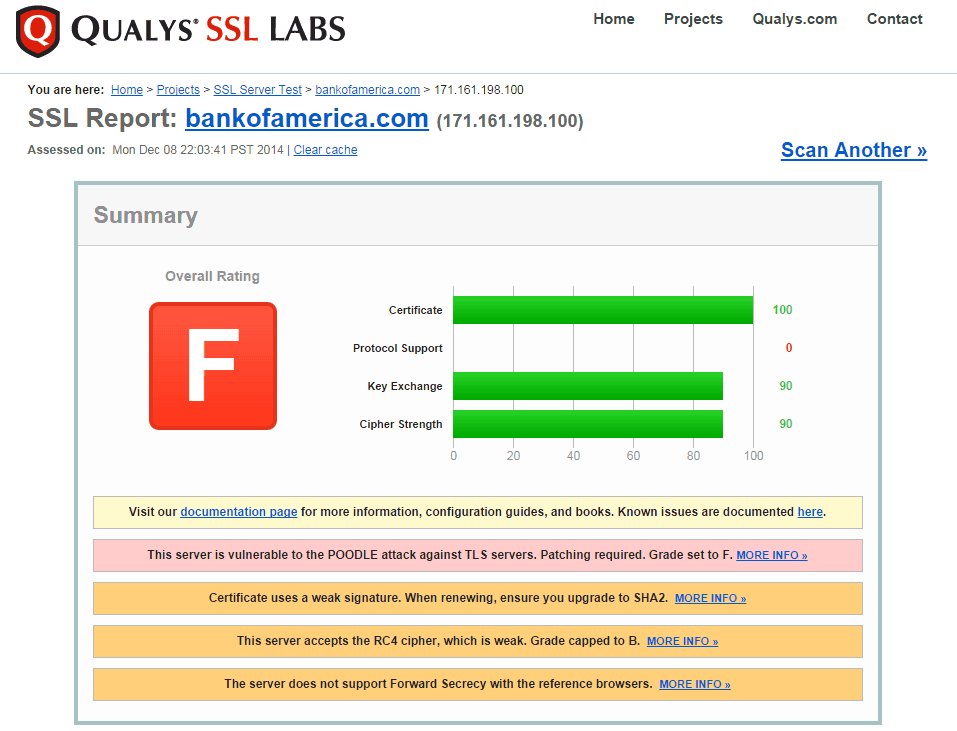
Monday, discussion that a deadly variant of the POODLE attack came to light, surfacing that an attack worked against a widely used TLS implementation. During this time, SSL Server Test, a free service that allows the public to test the security of HTTPS certificates, protocols and more related to encryption, has added support for POODLE variant testing. With the latest of release of the brutal POODLE variant, SSL Server test provided by security firm Qualys showed that some of the largest sites including Bank of America, the US Department of Veterans Affairs, VMWare and hundreds of others are vulnerable to the attack.
The attack was so serious SSL Server Test left some of the worlds leading sites with a failing grade by the security firm.
The original POODLE attack was an extreme security concern to many, but the steps required to initiate the attacked poised a many real-world events that would make executing the attack extremely difficult. Attackers had to spoof packets, modify transactions, and complete a number of tedious steps. Through the attack hackers could often steal security tokens and gain access to accounts or restricted sections of sites with the stolen data. The latest POODLE variant attack against TLS remains similar, except that it is slightly easier and requires less steps to carry out a successful attack to exfiltrate data.
“The impact of this problem is similar to that of POODLE, with the attack being slightly easier to execute—no need to downgrade modern clients down to SSL 3 first, TLS 1.2 will do just fine,” Ivan Ristic, Qualy’s director of Application Security wrote in a blog post titled POODLE bites TLS. “The main target are browsers, because the attacker must inject malicious JavaScript to initiate the attack. A successful attack will use about 256 requests to uncover one cookie character, or only 4096 requests for a 16-character cookie. This makes the attack quite practical.”
Thus far, only two different manufacturers of load balancers and similar items have been identified as vulnerable by security researchers. What makes the sites vulnerable is a recent versions of TLS call for encryption padding to be closely checked for what is called Oracle attacks, yet companies implementations skip these steps leaving them vulnerable to the POODLE variant exploit. Companies have begun issuing advisories detailing how products can be patched, specifically F5, one manufacturer who was found vulnerable. Another susceptible provider, A10, has yet to issue patches for their product.
Ristic estimates about one in ten websites across the web are vulnerable to the new POODLE variant attack against TLS. This means ten percent of the internet is susceptible to man-in-the-middle attacks, leaving a reasonable chance of attackers being able to bypass popular encryption implementations.
Others can freely test if sites are vulnerable with SSLLabs free SSL Server Test tool.
Administrators are advised to update their sites immediately insuring users are not vulnerable to the latest POODLE attack.