Android Ransomware, ScarePakage, Locks Phone Appearing to be the FBI
A new Android ransomware has begun targeting users in the United States, if infected, it will hold the phone hostage appearing to be the FBI extorting money from users.
Cybercriminals have recently ramped up ransonware campaigns online, not only has there been an influx in malware but actors have been appearing as the FBI, police, government agencies, and various other law based professions in their campaigns. In nearly all ransomware campaigns, the computer or device will be held hostage and a large sum of money will be demanded. If the fee is not paid, the ransomware generally holds the computer or device hostage while keeping the files encrypted meaning all files are inaccessible til’ paid.
In recent events, cybercriminals have begun attacking the mobile market with the same scams that have been targeting computers for years. Only one month ago, attackers built the first ransomware that encrypted the mobile device demanding money to re-gain access and decrypt the phone.
A new Android ransomware dubbed, ScarePakage, is a piece of malware being masqueraded into well-known applications, such as Adobe Flash and various anti-virus applications, that will pretend to do its job upon launch, Lookout mobile security reported. Upon the applications fake scan completion, the phone is immediately locked and an FBI ransomware image appears.
The ransomware appears with the following message:
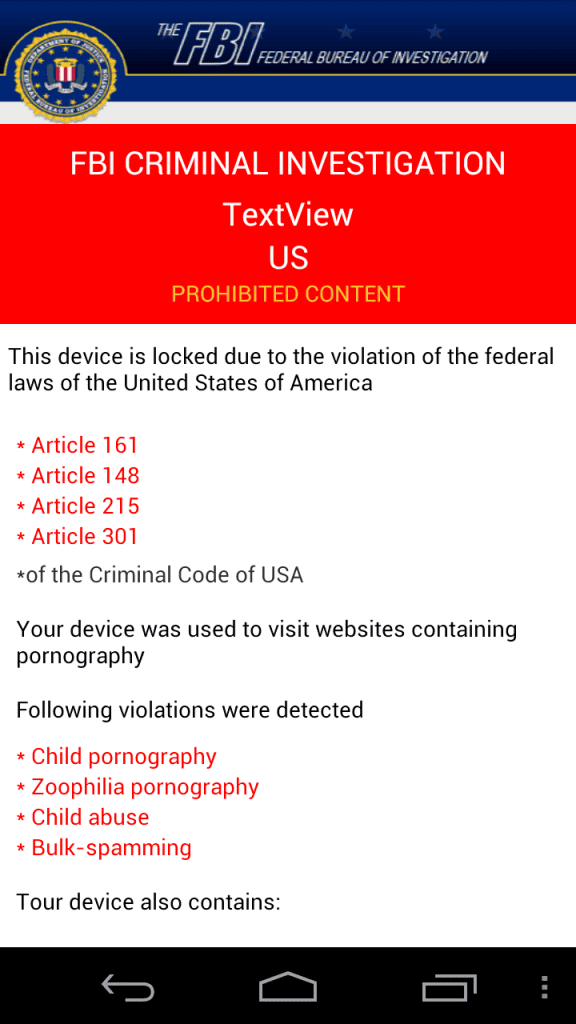
If you cannot see the image above, it reads:
FBI Criminal Investigation
TextView
US
Prohibited ContentThis device is locked due to the violation of the Federal laws of the United States of America
- Article 161
- Article 148
- Article 215
- Article 301
*of the Criminal Code of the USA
Your device was used to visit websites containing pornography
Following violations were detected
- -list of pornography violations-
The ransomware locks the phone meaning users cannot navigate away from the message. If the phone is rebooted, the FBI ransomware screen will be the first thing that appears.
ScarePakage demands users to pay a fee of $500 via a MoneyPak voucher to re-gain access to the device, researchers regarded how this is targeting the consumer market more than businesses or other high profile personnel. Lookout also found that the application performs a validation check to see if the code is long enough, but not if the code actually works. For the phone to be held hostage, it does not need to be rooted, the device simply needs administrator access.
ScarePakage Distribution Methods
“Currently, this threat appears in Android applications that claim to be Adobe Flash Player or Norton Internet Security, we believe that it is distributed through spam or ‘drive-by-downloads’ where the malware author either compromises existing websites or attracts the user to his own website (perhaps using advertising or pornography) after which the malware is downloaded to the user’s device. After the malware is downloaded, the user would still have to install the application on his device,” Jeremy Linden, Senior Security Product Manager at Lookout security told FreedomHacker in an email.
As the malware is still in it’s first rounds of distribution, it appears to require the installation of a malicious application so it can gain admin access to then take over the phone.
How it works
The intrusive ScarePakage malware blocks access to normal device-use with a specially crafted application. The malware uses a Java TimerTask, which is set to run every 10 milliseconds, the application then begins killing all other applications, running processes, or anything that is not affiliated with the malware itself or the phone’s settings application. The malware also uses an Android WakeLock to prevent the screen from dimming or going to sleep.
The malware makes turning the phone off a difficult task, but if completed and turned back on, a boot receiver class immediately resumes ScarePackage’s hostage of the device, again, shutting down all other processes users would normally have access to.
While ScarePackage does infact kill all processes, the plus side is it does not encrypt the device, Linden told us. Meaning the malware could be removed along with all files still being intact.
Similar to other found ransomware, ScarePakage may steal the users IMEI number and display it on the screen stating “We know who you are.” as a scare tactic and to presumably expedite the extortion. Lookout also found that in some instances ScarePackage sends the IMEI back to its command-and-control (C&C) server to identify the device.
ScarePakage is noted to have similar functionality to another ransomware dubbed ColdBrother, also known as Svpeng. ColdBrother can take photos using the front-facing camera, can answer and immediately drop phone calls, and has the ability to search for banking applications found on the device.
How to prevent ScarePakage
Linden told us that over 28,000 consumers encountered this malware in the first week. As the malware takes administrator privileges on the device, Linden states it is extremely hard to remove the ransomware. The following steps can help prevent the ScarePakage takeover:
- Avoid awarding device administrator to applications unless you are completely sure of what they do
- Only download applications from developers you know and trust
- Download a mobile anti-virus program, which can detect these threats before they are downloaded or executed






I just did a factory reset from the booting menu and it fixed it, but deleted all of my data, its a good think we have Cloud.
Yeah that will defiantly fix it as it wipes the phone clean. Glad to see it is now fixed!
Once it has taken over your device, how does one remove it? Or can someone even do that?
It depends. One mobile antivirus, ESET, built a tool to decrypt Simplocker. It is not ScarePakage as mentioned in this article, but that is the closest any company has come to decrypting the files. Other than that, victims can try removing it by hand or decrypting it themselves, but risk loosing all the data on the device. Lastly, if users pay, there is no guarantee that the device will unlock.
In the end, the way to remove it depends on what risks can be taken.
Thank you for this well-researched and informative article.