Syrian Electronic Army Hacks and Defaces RSA Conference Website
Pro-Syrian hackers known as, Syrian Electronic Army, recently hacked and defaced the RSA conference website shortly after a conference on the group went live.
The official RSA conference website, rsaconference.com, was taken down and defaced early Saturday after an RSA conference on the Syrian Electronic Army was presented. Ira Winkler presented the conference with “Syrian Electronic Army: Their Methods and Your Responses“. Shortly after Winkler’s talk went live on the RSA conference website, the Syrian Electronic Army took down and defaced the website.
Ira Winkler’s presentation talked about the Syrian Electronic Army attack vectors, and how to prevent them. Throughout the conference, Winkler calls the Syrian Electronic Army “stupid”, “low-tech”, “almost computer illiterate”, and a variety of other names. In one statement Winkler regards “these people are the cockroaches of the internet at the moment”.
After Winkler presented his Syrian Electronic Army presentation, the Syrian Electronic Army hacked and defaced the rsaconference.com website. The defaced website read
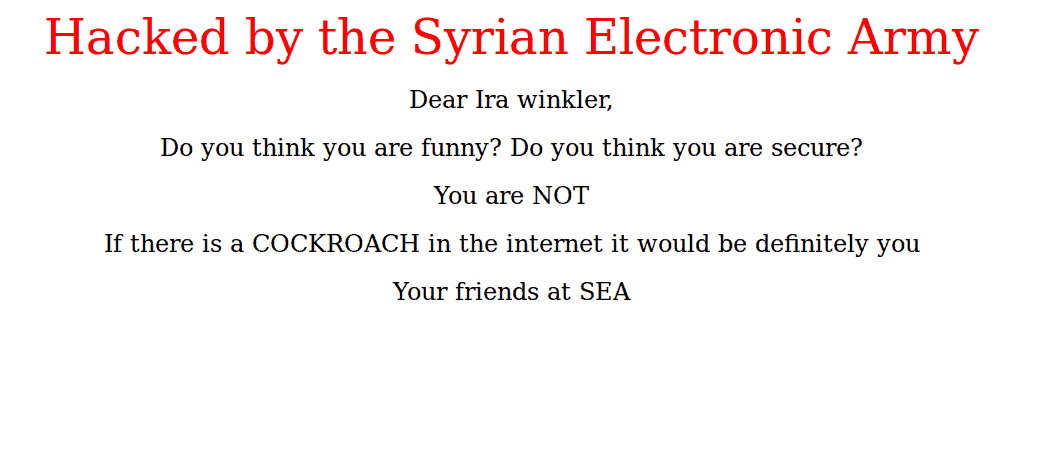
Hacked by the Syrian Electronic Army
Dear Ira Winkler,
Do you think you are funny? Do you think you are secure?
You are NOT
If there is a COCKROACH in the internet it would be definitely you
Your friends at SEA
The Syrian Electronic Army then tweeted links to Winkler reading “We were enjoying our summer peacefully, but the annoy of cockroaches like @irawinkler and other security firms led to 3 reports about #SEA.”-tweet and “Hi @irawinkler, There is a message for you on http://www.rsaconference.com/ , http://archive.today/KnsPn #SEA”-tweet.
On Monday Winkler wrote a blog post on how the Syrian Electronic Army defaced the RSA Conference website, noting it “How the ‘Hack’ Occurred”. The group found that visiting the website with JavaScript enabled triggers an analytic platform, Lucky Orange, to start. From there the group figured out what DNS server Lucky Orange was using, and found it to be locked. After not begin able to access the DNS provider, the group targeted current and former employees working for Lucky Orange found on LinkedIn. Syrian Electronic Army launched a spear phishing attack, the phishing email came from the CEO telling employees to read an alleged story about Lucky Orange that had been posted on the BBC. An account executive fell victim and the SEA had credentials to access the customer account management system. Once they had access, the #SEA reset the Lucky Orange login credentials and logged on as Lucky Orange Staff. From there the Syrian Electronic Army set the JavaScript file to execute window.location = “http://example.com/xxxx.png“ (real image retracted) instead of the analytic platform. When accessing the website with JavaScript enabled, the defacement image appeared. Other websites such as memorybook.com that were using the Lucky Orange analytic platform also received the defacement image on their website.
Ira Winkler covered how the domain wasn’t in full hacked and how it all happened, calling the attack “simple and basic.” Ira Winkler’s full talk on the Syrian Electronic Army cam be found on the RSA Conference website, or below.







This is awesome. xD