How to Check and see if your VPN Connection is Secure
How to Check and see if your VPN Connection is Secure
VPN’s can be very easy or complex to set up. They may even be so easy that you don’t know if they are running correctly, or even protecting you. Today you are going to be able to test your VPN connection, and see if it’s actually secured. When you turn on a VPN it is very simple, you may just hit connect, it tests the connection, then finally connects. But is it really securing that connection and encrypting it? Is your ISP getting leaked queries? Check and see if your VPN Connection is Secure…
What is the VPN suppose to secure?
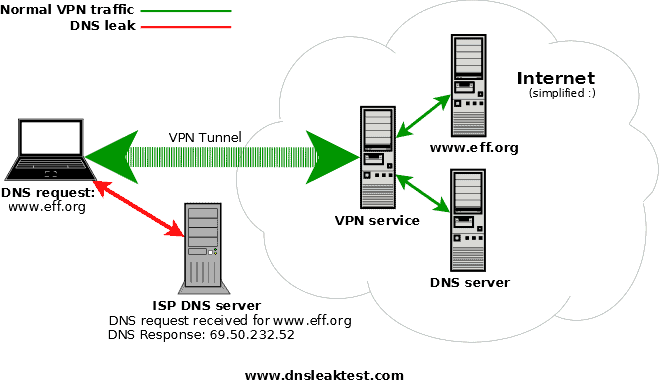
A VPN can be quite complex, but I will just be going over a few things your VPN should protect. A VPN consists of an IP address, a DNS, and keeping everything inside their given IP and DNS. This means that when you connect to YouTube.com, the VPN should secure your entire connection, even when using flash. Once connected, you should be assured that flash player queries are not getting leaked a from your real computers IP to identify you. This also applies with Java. When playing games with Java, is your real computer or location identifiable? And on top of keeping these applications secure, the VPN needs to keep all your DNS queries within the VPN’s given DNS. This is where MANY VPN providers fall short. Most VPN providers offer no protection against DNS leaks (except Private Internet Access), and most don’t even mention it. DNS leaks are a huge security flaw. Most if not all of your http:// queries can be leaked to your ISP. The picture below will show you what a DNS leak looks like.
As you can see, a DNS leak can be a huge vulnerability. It doesn’t defeat the purpose of a VPN, but it still tells your ISP what websites you visit. A VPN’s objective is to secure you from your ISP, and keep your traffic hidden. If your service provider is still seeing what websites you visit, it defeats the entire purpose as your ISP is still logging your data.
How can I see if my VPN is working, and securing me?
There are many tools online to check this, but there are not many that do it right. Below I will list some of the best tools to check your VPN configuration with. If you notice any leaks, or that your VPN is not working properly, some solutions will be listed below.
- IP address test – To start, go with a simple IP check. Make sure that the location shown on the map is not your actual home location, and that it’s your VPN providers server.
- Extended IP address test – This test is where it really counts. This checks your Flash, Java, and DNS. Make sure the flash, and java IP’s/DNS’s are not yours leaking and ensure they are the VPN providers. Check the IP’s and put them into a search engine like DuckDuckGo. Many VPN providers point their DNS to Google. Google is located in Mountain View, California. But if the DNS leaks something similar to 127.0.0.1.verizionfios.direct, and you are using Verizion fios, your queries are begin leaked.
- IP test for Bittorrent (old site – Delinked for security reasons) (now dead)- This will test your Bittorrent/P2P IP. Once you hit start, it will download a test .torrent file. Open the .torrent file in your bittorrent client. Once opened, let it connect and download. Once it does, the website should tell you what IP is begin shown to others in a bittorent swarm. It should be showing your VPN’s IP.
- DNS leak check (here is another optional checker)- Probably one of the most important ones aside from the VPN begin connected. Check for possible leaks. Click check, and let it load the IP’s/DNS’s. If any point to your home DNS, or look something like 127.0.0.1.verizionfios, your queries are begin leaked to your ISP. Again, if your don’t notice them, check the IP on DuckDuckGo. If they are right next to your real location, most of the time, queries are begin leaked.
My VPN is leaking, how can I fix this?
If anything is begin leaked, its better to fix it sooner than later. First off, your IP. If your VPN is turned on and your real IP is still begin leaked, check again. Make sure the VPN is turned on, or that the client is installed correctly. If you are using OpenVPN make sure you have the cert. in the right place. Go through the VPN pages FAQ, and make sure you have it on. If its still begin leaked and you are %100 confident its on, contact the support team, or get a refund.
If your Flash or Java is getting leaked, it probably fits in with the DNS leaks. But just for extra security, be sure you are using SSTP/OpenVPN protocol. Its the most secure, and most VPN providers offer it. If not, PPTP, and L2TP protocols are worthless. Even if you are using your VPN on Android, or iOS MAKE SURE they support OpenVPN. There are OpenVPN apps for both. The top 2 providers that offer it are AirVPN, and Private Internet Access.
If your bittorent IP is begin leaked it may have to do with your DNS in part. But if not, make sure you have it set up correctly. Make sure you have your ports set up correctly, and you are using a reliable client. If it continues to leak again, check if the VPN is on. If this persists, it could be a DNS leak, or very poor quality VPN that cannot hold connections (I have had a few that did this in the past).
Lastly, if you have DNS leaks. This is the most common problem, and the fix is simple. Either point your DNS to a free non-logging DNS, or choose what you want to use. I choose to use ones I can personally choose. For one, you can download dnsfixsetup.exe (from DNSLeaktest.com) which will stop DNS leaks for you automatically. But, I choose to use DNSBench which is a manual option. Someone on Reddit recommended:
I prefer using fat pipe providers like level-3 and global crossing since they are not in the metadata business.most will tell you to simply use the default dns offered by your VPN provider at the outlet country you selected.
having the ability to log you is worthless if you are on a shared public ip from your vpn provider, so don’t worry
about that warning message. only worry if your dnsleaktest shows servers with your ISP’s own name on them.
I tested this out, and it worked great! I tested some fast, non-logging DNS’s not run by big corps and they work great. I just have to set my adapter to a new one if I want to change. It is quite simple, and I use this method. If you are using windows, follow my guide HERE. Follow step one, and instead of using “Obtain DNS server address automatically“, put in the DNS that you wanted to use from DNS bench into the use the following address field. Once this is done, wait for your internet to reset itself, and possibly reset the VPN too. Once this is done, go do the tests again. You should not experience any leaks, and should be fully secured. If you continue to find problems talk to the VPN provider.
Overall
Overall you need to secure your DNS. To many DNS leaks occur, and your internet provider still blatantly laughs at you. Private Internet Access’s client allows a one click Stop DNS leaks option. If you don’t want to mess around with the settings be sure the test them out at PrivateInternetAccess.com. Check your VPN connection, and make sure you are secured!







Let me reccomend you one more service which is pretty good and is able to check connection’s anonimity by running 15 different tests on it: https://2ip.io/privacy/
Hey thanks for the comment. We checked it out and this is an awesome tool! Defiantly very intensive.
I am going to get in on this! Your page title states “How to Check and see if your VPN Connection is Secure” in this post you state conducting an IP info test & dns leak-test is sufficient enough to verify a secure connection. I am not scolding you I simple think you are misleading the public with false information. And a false sense of security. Now it appears as you don’t know what you are talking about. Your entire page is leading people to believe that because their ip and dns have changed that now some how they are secure. And to be honest none of those statements prove any thing, and least of all that some one has a secure vpn connection.
1. IP INFO TEST DO NOT PROVE YOU HAVE A SECURE VPN CONNECTION.
2. DNS LEAK TEST DO NOT PROVE YOU HAVE A SECURE VPN CONNECTION.
Hello again, yes we are aware of what you are saying. However, we feel this is a basic and simple test for people to check if their VPN is masking their IP. Not everyone knows how to open wireshark and sniff their network.
Again we are aware of what your saying and do agree.
Conducting a dns leak test has no bearing nor does it verify that your vpn is encrypting your data, this is an absolute wast of time and provides people with a false sense of security. Any one can change their dns on their client machine with out a vpn. Please explain in any rational terms how you believe an dns leak test verify s a successful vpn encryption connection? I am excited to hear your explanation!
Hello, we in no way claim this ensures your VPN is encrypting you connection. As stated, this test ensures your VPN is masking your identity, such as IP address and plugging any DNS leaks. You’re always welcome to pop open wireshark and sniff your own connection.
Most VPNs leak. The conspiratory side of me suspects a NSA demand that they have to, the more plausible side says blatant incompetence. There are “hacks” and scripts to correct it in abundance, so it can be done in a jiffy. For starters make, sure ISP is of the kind that doesn’t hand out information on your surfing habits. The same goes for the VPN provider. Make sure the VPN is encrypted and transparent. Get an encrypted transparent proxy. Last and perhaps use a browser that stops g**gle from collecting any data on your surfing habits. The last one is crucial as there are very good algorithms to pinpoint you other-ways. I strongly recommend Epic Privacy Browser, as it stops that and is very secure.
Lifts foil hat to let some dandruff out…
Seems very plausible, however I believe the NSA just collects amass of information, encrypted or not, and then really targets and tries to crack only high-profile targets communications. I doubt unencrypting Americans ISP logs are their top priority, meaning they just use their “collect it all” motto.
However, I do agree Epic Privacy Browser is great, highly recommend it for easy-to-use private browsing.
I would take it a step further and employ the Aviator browser, which by default, also protects users privacy and is faster. It is also more user-friendly and has additional security features that Epic does not. Cyberfox is also another great alternative too, as is Comodo’s Ice Dragon.
And while we’re on the subject of browsers, lets not forget if you’re a Windows user and have not yet disabled Internet Explorer as well as removing from your “Default Programs” startup, then you’re still leaving yourself slightly more vulnerable even if you choose not to use that browser. Disable it as well as any other services used by Google or Microsoft for the collection of information (unless the Microsoft service gives clear warning that disabling a service will cause critical components to stop working). You really don’t need to have anything Google on your machine. It is a ploy to aggregate your data for their purposes ultimately circumventing your rights to true privacy.
Additionally and most importantly, harden your system security by employing supplemental security programs such as [ Latest version of EMET from Microsoft ], [ HitmanPro.Alert ], [ Zemana Antilogger ], [ TinyWall ], [ RUBotted ], and [ Malwarebytes AntiMalware ] to name a few.
Yes you can run all those programs on your computer at once, you just have to know what you are doing. Yes HitmanPro.Alert is similar to EMET and in a lot of ways more comprehensive, however with EMET installed, it can act as a first line of defense (depending on how you configure it), subsequently followed by the protections and mitigations of your other security applications.
The idea here is to layer your system security and to do this you need to know how to program any necessary exceptions between. Most of the aforementioned security apps are already designed to avoid compatibility issues with other security software. So really, you don’t have to do much once they’re installed.
If you’re a computer geek and can understand concepts such as ASLR, SEHOP, and HEAP protection——-then you’ll obviously have a leg-up on really tweaking these applications to provide maximum protection.
Of course, no security approach is 100%, but if you follow good computing practices, exercise common sense, air on the side of caution when using any personal information online and take appropriate steps to harden your system security, then you’ll be far better off for it…
Great subject and instructions with only one caveat…
If you are on a VPN then would it not be more secure to use the VPN’s DNS servers rather than risk lets say using Googles which might defeat the object of remaining ANON at the entry or exit to the VPN ?
Hi Bob, great question! This has been a controversial subject for some time, but we have always stayed put on our answer, be sure you are using a secure DNS. By that we mean a DNS that respects privacy and is secure from outside attacks and interception.
The issue with Google is they log all your data, but seeing as you may only be using them for a DNS server, Google would only be able to see you visited example.com from the VPN IP address, not resulting in a huge privacy breach, but your still handing them more data than is necessary. One benefit of Google DNS is it is fast and extremely secure, making it a #1 option for most.
Personally, we stick to VPN providers who use their own DNS servers. Many providers exist and if you need any recommendations or help feel free to contact us again. Hope that helped!
Thanks for the information – I have been using PIA for a couple of years and the tests which you recommend I have done on a regular basis and PIA have never let me down. We have to trust the VPN provider when they say they do not log – that is one test we cannot replicate.