TrueCrypt Secure, Encryption Tool Passes First Audit With No Backdoors
TrueCrypt the popular freeware to encrypt hard drives and operating systems ranging from Linux, to Mac OSX, to regular Windows had been under heat for some time. The public believed that the freeware encryption tool may be easily cracked or a government operation. Well, TrueCrypt has successfully passed its first audit phase.
Analysts have tested over 70,000 lines of the source code, and TrueCrypt has successfully passed its first audit. TrueCrypt is a popular freeware tool to encrypt virtually any operating system or hard drive. The tool is not the average file encryption tool. TrueCrypt allows for sectors of hard drives to be encrypted, full disk encryption, and built in hidden operating systems. TrueCrypt can initially create hidden volumes and boot to dummy operating systems. On top of the features, there is no master key. If a user forgets their encryption password, there is no master password to unlock the drive. The password one sets is the only password that will unlock the drive, and it cannot be recovered.
The anonymous developers of TrueCrypt run under aliases “ennead” and “syncon”. It is unknown why, and who they are, but this could be to avoid harassment, or government intervening. While this is great for the developers, this is a worry for the public. With the NSA, surveillance agencies, and governments backdooring products, the anonymity of the developers makes users weary.
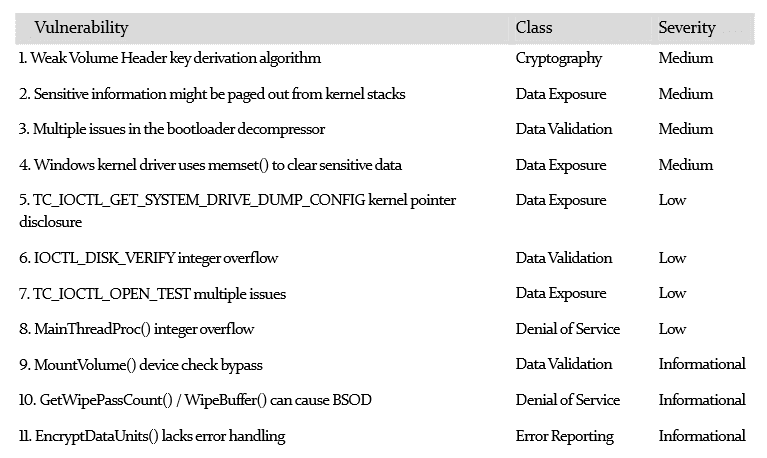
The popular freeware trusted by millions seems to have nearly a clean slate. Researchers at iSec Reseach Lab who were contracted to perform the audit has found “no evidence of backdoors or otherwise intentionally malicious code in the assessed areas.” Researchers did in fact find over 11 vulnerabilities in the software, but none that are critical. Through reviewing the TrueCrypt architecture no flaws were of “high-severity”.
Researchers stated none of found vulnerabilities seem to be intentional to flaw or help a third party exploit the software.
“Overall, iSEC does think changes can be made to improve code quality and maintainability, and that the build process should be updated to rely on recent tools with trustworthy provenance. In sum, while TrueCrypt does not have the most polished programming style, there is nothing immediately dangerous to report,” reads the released audit report.
The first audit phase focused on TrueCrypt’s boot loader and Windows kernel driver, or architecture and code review.
TrueCrypt Audit Phase 2
TrueCrypts second audit will focus on encryption cipher suites and implementation of random number generators and critical key algorithms. Thousands of dollars have been put into this audit and researchers are deeply reviewing all sectors of TrueCrypt. The community along with ourselves truly hopes phase two turns out similar to phase one.