Vault 7: Marble Framework Reveals How the CIA Evaded Forensics & Attributed Malware to Other Countries
Wikileaks has published part 3 of Vault 7, a multi-part leak revealing a previously undisclosed and extensive CIA hacking arsenal. The organization revealed that the CIA has dozens of unclassified hacking units with an arsenal of weaponized hacking tools. The latest leak reveals how the CIA was able to penetrate systems while remaining completely anonymous, with the ability to actively attribute the hack to another country or author.
Marble, the name of the latest Wikileaks dump, reveals “676 source code files for the CIA’s secret anti-forensic Marble Framework. Marble is used to hamper forensic investigators and anti-virus companies from attributing viruses, trojans and hacking attacks to the CIA.”
The framework worked by hiding text fragments written by the CIA in their own malware, allowing them to easily cover up their own footprint. This also allowed the CIA to place cover over the fact that the malware was written in the English language and produced as a weaponized backdoor for an intelligence agency.
The Marble framework is a core principle within the CIA’s malware development sector. The ability to deflect the attribution of an intrusion and point it to another author is breathtaking. According to the CIA, it is “designed to allow for flexible and easy-to-use obfuscation” as “string obfuscation algorithms (especially those that are unique) are often used to link malware to a specific developer or development shop.”
Marble’s source code reveals that the CIA had test examples not just in English, but also in Chinese, Russian, Korean, Arabic and Farsi. This would permit the CIA to attribute the malware to another author or make it appear to be written by someone of another spoken language. The leak reveals the CIA implanted decoy language within the code. Deflecting forensic investigators to believe the malware author was not English, but instead spoke Chinese or Russian. Drawing investigators to the wrong conclusion.
The framework was under constant development and reached version 1.0 by 2015. Wikileaks claims the CIA used Marble for hacking during 2016, however, targets were not specified.
How does Marble work
Marble is extremely complex and its main goal is “obfuscation.” Within the framework, the CIA had a number of techniques as well as an actual executable file to perform the task automatically.
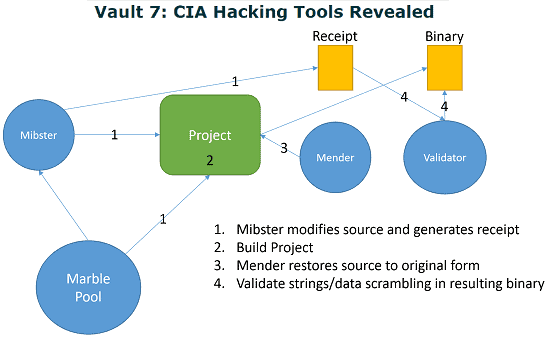
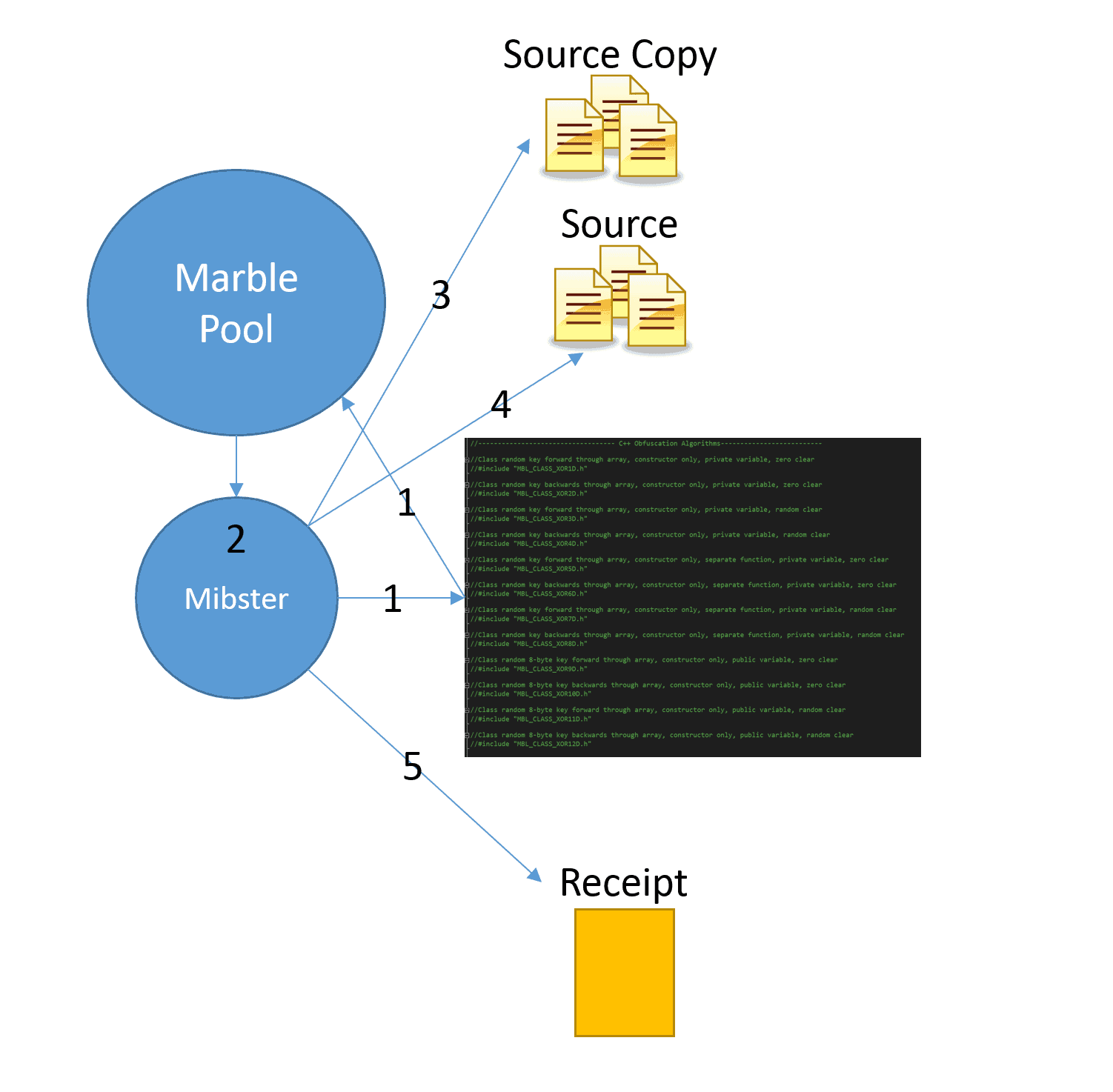
The framework is extremely detailed and takes 4 to 5 steps to entirely execute. It starts by scrambling and alternating sources files based on an algorithm chosen from the list. A utility called, Mibster, “keeps a clean copy of the original source and replaces it with the scrambled versions of strings/data as well as supplies the unscramble function.”
There are 6 different utilities that the CIA must use for the framework to fully execute, including Marble, Mibster, Mender, Warble, Carble, and Validator. However, Mibster takes a majority of the work. Mibster works in a combination of 5 steps:
- First it parses the Marble.h header file to generate a pool of available algorithms
- It then randomly chooses an algorithm from the pool and uses is to generate obfuscated versions of strings in source files. The Mibster verifies the scrambled string does not contain 3 consecutive characters that are the same as the original string (fails out if this is not true – Visual Studio error).
- Saves a copy of all source files that need modified. If it fails to create copies of the source, the Mibster fails out without modifying anything.
- Modifies all source by replacing the defined strings with an “insert” that is generated by the Marble.
- Generates a receipt file that contains the framework version, algorithm used, and strings that were obfuscated.
The three steps following Mibster are to ensure that the malware properly executes and is scrubbed of any CIA techniques.
The latest Vault 7 dump shows that the CIA had a huge amount of power with the ability to not only hack any system, but stage malware and intrusions from other parties. Marble could send forensic investigators down a total bogus path and have agencies blaming completely innocent countries for an entirely US-based intrusion.






this website is amazing, keep up !!!