TMZ.com Vulnerable to Heartbleed Nearly One Year Later
The worlds largest celebrity news and gossip blog, TMZ.com, was identified vulnerable to a severe OpenSSL vulnerability, Heartbleed, nearly a year after the vulnerability was initially disclosed.
Heartbleed, the security bug found in OpenSSL’s cryptographic library allows for hackers to potentially steal private keys allowing them to decrypt TLS connections on vulnerable versions of the OpenSSL protocol. Meaning hackers could easily hijack a website and all the data stored on the servers, including administrator credentials, the sites database, user credentials and more.
The vulnerability disclosed back in April 2014 is rising on the one year old mark, currently standing at 10 months old. At the time of disclosure, the vulnerability was catastrophic, leaving over 17% of the web at risk at time time, but security researchers helped OpenSSL fix the gaping security hole before notifying the public. This allowed for OpenSSL to release a patch the day the vulnerability was disclosed, allowing for webmasters and network administrators to patch their servers promptly.
TMZ.com being vulnerable to Heartbleed nearly a year later is still catastrophic, seeing as the site allows for users to register for accounts and interact with the community. This means all TMZ users credentials, such as emails and passwords could be at risk and breached from the server.
The Computer Emergency Readiness Team (CERT) at the Software Engineering Institute (SEI) have a strict vulnerability disclosure policy that allows for security researchers to properly disclose of vulnerabilities within 45 days if the company does not respond, and that’s just what one user did. CERT allows for vulnerabilities to be publicly disclosed as it helps further secure the Internet.
“Vulnerabilities reported to the CERT/CC will be disclosed to the public 45 days after the initial report, regardless of the existence or availability of patches or workarounds from affected vendors,” CERT writes in their vulnerability analysis and proper disclosure guidelines. “Extenuating circumstances, such as active exploitation, threats of an especially serious (or trivial) nature, or situations that require changes to an established standard may result in earlier or later disclosure.”
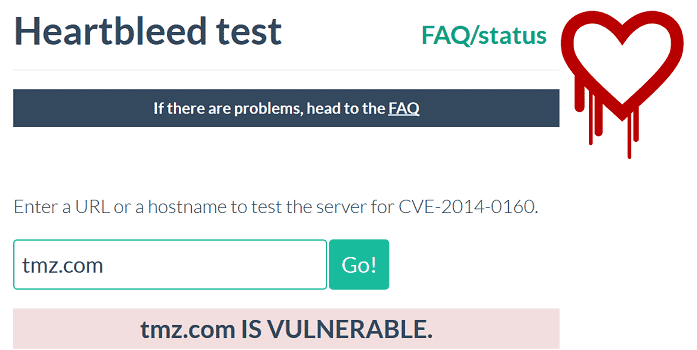
One anonymous redditor posted a link to an image in the hacking subreddit, showing TMZ.com being vulnerable to Heartbleed last Friday, dated February 6:
The tool used to test if TMZ.com was vulnerable to Heartbleed was the Heartbleed test, developed by security consultant Filippo Valsorda, and posted on his personal website. The site scans to see if the server is still vulnerable to the OpenSSL bug and gives proper guidelines on what is vulnerable and proper actions to take to secure the server.
A number of other Heartbleed test tools too identified TMZ.com as vulnerable. Lastpass’s Heartbleed checker shows TMZ was no longer vulnerable to Heartbleed nearly six months ago, but research and tests show otherwise. The Lastpass tool only checks the date the sites HTTPS certificate was issued, deeming a site safe and not vulnerable if a certificate was issued post-Heartbleed. Too add, the site just recently moved to full HTTPS not to long ago.
Due to the large size of TMZ.com and their influence, a small number of redditors have already begun brewing up conspiracies regarding the topic, saying TMZ might have already been compromised leading to the potential attacker being able to delete the emails sent to TMZ.
As of the time of writing this article, TMZ.com is still vulnerable to Heartbleed February 8, 2015.
The user who initially disclosed that TMZ.com was vulnerable to the Heartbleed bug nearly a year later said the site lacks private contact information. The user claimed the only way to get in contact with TMZ is through a public web contact form.
Which further led to more conspiracies and jokes regarding how to get in contact with TMZ privately.
Just two months after the Heartbleed disclosure we saw over 300,000 servers still vulnerable to the bug, including some major sites.
Though content on TMZ.com is free, the vulnerability, if properly abused, could allow for hackers to steal large amounts of sensitive data belonging to users, administrators, and even editors on the site.